Computers and Technology, 18.12.2019 19:31 helo55
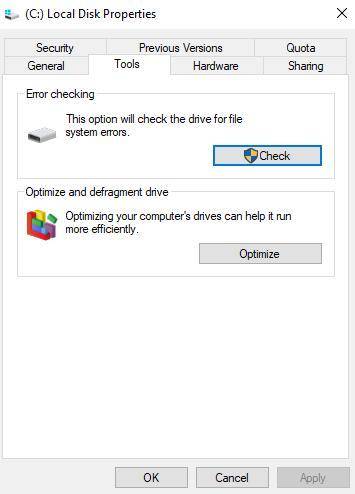
Case 2-2 jack has a computer at home that he uses to access the internet, store and edit personal photos, and create and edit documents. recently, he has come to realize that in order to keep the computer performing at its best, he needs to carry out regular system maintenance on the computer. since jack has a windows system, he can right-click a hard drive icon in file explorer, select properties, and then select the option on the tools tab to check that hard drive for errors.

Answers: 3


Another question on Computers and Technology

Computers and Technology, 22.06.2019 10:30
Dave has to create animations for a game. which tool can dave use?
Answers: 3

Computers and Technology, 22.06.2019 16:50
Consider a slotted aloha system, where the time slot equals the fixed duration of each packet. assume that there are 4 stations a,b,c,d sharing the medium. (a) stations a,b,c,d receive one packet each from higher layers at times 1.3, 1.5, 2.6,5.7 respectively. show which transmissions take place when, according to the slottedaloha protocol; describe all transmissions until all four packets have been successful.when needed, each station has access to the following sequence of random number, provided by a random number generator and drawn uniformly between 0 and 1: (1) station a draws numbers: 0.31, 0.27, 0.78, 0.9, 0.9, 0.11, 0. (2) station b draws numbers: 0.45, 0.28, 0.11, 0.83, 0.37, 0.22, 0. (3)station c draws numbers: 0.1, 0.2, 0.3, 0.4, 0. (4) station d draws numbers: 0.36, 0.77, 0.9, 0.1, 0.1, 0.1, 0.1, 0. (b) in slotted aloha, a station transmits in each time slot with a given probability. what probabilities would you assign to each of the four stations so as to: (i) maximize the efficiency of the protocol? (ii) maximize fairness among the four stations? (c) will the efficiency increase or decrease if we modify slotted aloha as follows: (i) get rid of slots and allow stations to transmit immediately? (ii) implement carrier sensing? (iii) implement collision detection? (iv) implement collision avoidance?
Answers: 3

Computers and Technology, 23.06.2019 10:30
How would you categorize the software that runs on mobile devices? break down these apps into at least three basic categories and give an example of each.
Answers: 1

Computers and Technology, 23.06.2019 11:30
Auser is given read permission to a file stored on an ntfs-formatted volume. the file is then copied to a folder on the same ntfs-formatted volume where the user has been given full control permission for that folder. when the user logs on to the computer holding the file and accesses its new location via a drive letter, what is the user's effective permission to the file? a. read b. full control c. no access d. modify e. none of the above
Answers: 1
You know the right answer?
Case 2-2 jack has a computer at home that he uses to access the internet, store and edit personal ph...
Questions

History, 05.05.2020 05:57



Social Studies, 05.05.2020 05:57

Mathematics, 05.05.2020 05:57


Biology, 05.05.2020 05:57


Mathematics, 05.05.2020 05:57


History, 05.05.2020 05:57


Advanced Placement (AP), 05.05.2020 05:57

Mathematics, 05.05.2020 05:57