
Computers and Technology, 26.12.2019 00:31 babygirlgabby2137
One of the earlier applications of cryptographic hash functions was the storage
of passwords for user authentication in computer systems. with this method, a
password is hashed after its input and is compared to the stored (hashed) reference
password. people realized early that it is sufficient to only store the hashed versions
of the passwords.
1. assume you are a hacker and you got access to the hashed password list. of
course, you would like to recover the passwords from the list in order to impersonate
some of the users. discuss which of the three attacks below allow this.
exactly describe the consequences of each of the attacks:
attack a: you can break the one-way property of h.
attack b: you can find second preimages for h.
attack c: you can find collisions for h.
2. why is this technique of storing hashed passwords often extended by the use
of a so-called salt? (a salt is a random value appended to the password before
hashing. together with the hash, the value of the salt is stored in the list of hashed
passwords.) are the attacks above affected by this technique?
3. is a hash function with an output length of 80 bit sufficient for this application?

Answers: 2


Another question on Computers and Technology

Computers and Technology, 22.06.2019 16:10
When copying and pasting text, the first step is move your cursor type the text select the copy command select the paste command
Answers: 2

Computers and Technology, 23.06.2019 17:00
The more powerful, 60 volt cables and the main power shut off on an hev are both colored orange
Answers: 1

Computers and Technology, 23.06.2019 21:20
In microsoft word, when you highlight existing text you want to replace, you're in a. advanced mode. b. automatic mode. c. basic mode. d. typeover mode
Answers: 1

Computers and Technology, 24.06.2019 04:30
1. web and mobile applications allow users to be actively engaged in an online activity. a true b false 2. some examples of business applications purposes are to collaborate, share files, meet virtually in real-time, and accept payments. a true b false 3. an education application would most likely do which of the following? a allow users to watch popular movies and tv shows b connect users with social and business contacts c confirm users' travel plans d teach users a new language 4. a uniform resource locator (url) is how the internet knows where to take users when an address is typed into a browser. a true b false 5. deon is required to provide the citation information for his sources. what type of information should he collect from his sources? a author name, title, date of publication, date of access, url b connections to background information c interesting facts and statistics d notes on important information
Answers: 1
You know the right answer?
One of the earlier applications of cryptographic hash functions was the storage
of passwords f...
of passwords f...
Questions


History, 21.08.2020 21:01




English, 21.08.2020 21:01





Mathematics, 21.08.2020 21:01


English, 21.08.2020 21:01


Physics, 21.08.2020 21:01


Mathematics, 21.08.2020 21:01



Mathematics, 21.08.2020 21:01

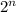 . It requires the attacker to have an idea about the kind of passwords that might be used and then brute force all of them to find string that has the same hash. Each try will have a chance of 1/
. It requires the attacker to have an idea about the kind of passwords that might be used and then brute force all of them to find string that has the same hash. Each try will have a chance of 1/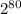 different hash values. This means there is at least one collision if
different hash values. This means there is at least one collision if 

