
Computers and Technology, 12.08.2020 08:01 mcmccann4317
Generating a signature with RSA alone on a long message would be too slow (presumably using cipher block chaining). Suppose we could do division quickly. Would it be reasonable to compute an RSA signature on a long message by first finding what the message equals (taking the message as a big integer), mod n, and signing that?

Answers: 1


Another question on Computers and Technology

Computers and Technology, 22.06.2019 11:00
The great length of north america causes the climate to be varied. true false
Answers: 2

Computers and Technology, 23.06.2019 01:40
You have a linux system that has a 1000gb hard disk drive, which has a 90gb partition containing an ext4 filesystem mounted to the / directory and a 4gb swap partition. currently, this linux system is only used by a few users for storing small files; however, the department manager wants to upgrade this system and use it to run a database application that will be used by 100 users. the database application and the associated data will take up over 200gb of hard disk space. in addition, these 100 users will store their personal files on the hard disk of the system. each user must have a maximum of 5gb of storage space. the department manager has made it very clear that this system must not exhibit any downtime as a result of hard disk errors. how much hard disk space will you require, and what partitions would you need to ensure that the system will perform as needed? where would these partitions be mounted? what quotas would you implement? what commands would you need to run and what entries to /etc/fstab would you need to create? justify your answers.
Answers: 3

Computers and Technology, 23.06.2019 02:00
Which of the following is not a source of sustainable raw materials? a) coal mine b) flick of sheep c) cotton plantation d) line forest.
Answers: 2

Computers and Technology, 23.06.2019 15:20
An ou structure in your domain has one ou per department, and all the computer and user accounts are in their respective ous. you have configured several gpos defining computer and user policies and linked the gpos to the domain. a group of managers in the marketing department need different policies that differ from those of the rest of the marketing department users and computers, but you don't want to change the top-level ou structure. which of the following gpo processing features are you most likely to use? a, block inheritance b, gpo enforcement c, wmi filtering d, loopback processing
Answers: 3
You know the right answer?
Generating a signature with RSA alone on a long message would be too slow (presumably using cipher b...
Questions

Mathematics, 12.10.2020 06:01

History, 12.10.2020 06:01

Computers and Technology, 12.10.2020 06:01


English, 12.10.2020 06:01

Chemistry, 12.10.2020 06:01

Spanish, 12.10.2020 06:01



History, 12.10.2020 06:01

Mathematics, 12.10.2020 06:01



Mathematics, 12.10.2020 06:01

Mathematics, 12.10.2020 06:01

Health, 12.10.2020 06:01



World Languages, 12.10.2020 06:01

Mathematics, 12.10.2020 06:01

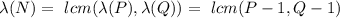 where
where 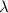 is the total function of Carmichaels. It is a privately held value. Selecting the integer E to be relatively prime from
is the total function of Carmichaels. It is a privately held value. Selecting the integer E to be relatively prime from 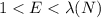 and
and 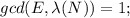 that is
that is 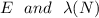 . D was its complex number equivalent to E (modulo
. D was its complex number equivalent to E (modulo 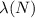 ); that is d was its design multiplicative equivalent of E-1.
); that is d was its design multiplicative equivalent of E-1. 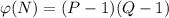 however, could even, as mentioned throughout the initial RSA paper, have been used to compute the private exponent D rather than λ(N).
however, could even, as mentioned throughout the initial RSA paper, have been used to compute the private exponent D rather than λ(N).
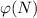 , which can always be split into
, which can always be split into 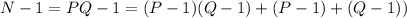 , it's also possible, if there are any, for all the common factors
, it's also possible, if there are any, for all the common factors 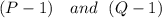 to become very small, if necessary.
to become very small, if necessary. 

