
Computers and Technology, 24.02.2021 19:50 janyiareese12
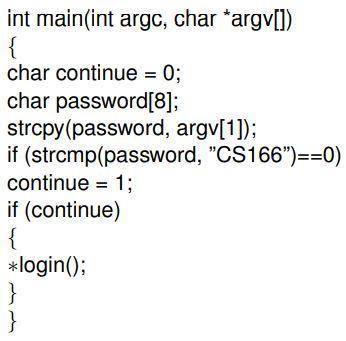
Consider the following piece of C code (in attachment):
In the above code, ∗login() is a pointer to the function login()
(In C, one can declare pointers to functions which means that the
call to the function is actually a memory address that indicates
where the executable code of the function lies). (1) Is this
code vulnerable to a buffer-overflow attack with reference to the
variables password[] and continue? If yes, describe how an attacker
can achieve this and give an ideal ordering of the memory cells
(assume that the memory addresses increase from left to right)
that correspond the variables password[] and continue of the code
so that this attack can be avoided. (2) To fix the problem, a security
expert suggests to remove the variable continue and simply use
the comparison for login. Does this fix the vulnerability? What
kind of new buffer overflow attack can be achieved in a multiuser
system where the login() function is shared by a lot of users (both
malicious and and nonmalicious) and many users can try to log
in at the same time? Assume for this question only (regardless
of real systems’ behavior) that the pointer is on the stack rather
than in the data segment, or a shared memory segment. (3) What
is the existing vulnerability when login() is not a pointer to the
function code but terminates with a return() command? Note that
the function strcpy does not check an array’s length.

Answers: 3


Another question on Computers and Technology

Computers and Technology, 23.06.2019 06:30
You are consulting for a beverage distributor who is interested in determining the benefits it could achieve from implementing new information systems. what will you advise as the first step?
Answers: 1

Computers and Technology, 24.06.2019 01:00
What are two ways to access the options for scaling and page orientation? click the home tab, then click alignment, or click the file tab. click the file tab, then click print, or click the page layout tab. click the page layout tab, or click the review tab. click the review tab, or click the home tab?
Answers: 2

Computers and Technology, 24.06.2019 15:50
Subscribe to j p g a m e t u b e on you tube ?
Answers: 2

Computers and Technology, 24.06.2019 17:40
The value of sin(x) (in radians) can be approximated by the alternating infinite series create a function (prob3_2) that takes inputs of a scalar angle measure (in radians) and the number of approximation terms, n, and estimates sin(x). do not use the sin function in your solution. you may use the factorial function. though this can be done without a loop (more efficiently), your program must use (at least) one. you may find the mod() function useful in solving the problem.
Answers: 1
You know the right answer?
Consider the following piece of C code (in attachment):
In the above code, ∗login() is a pointer to...
Questions

Mathematics, 30.08.2021 23:50

Physics, 30.08.2021 23:50





Social Studies, 30.08.2021 23:50

Mathematics, 30.08.2021 23:50



English, 30.08.2021 23:50

Physics, 30.08.2021 23:50

Mathematics, 30.08.2021 23:50

Biology, 30.08.2021 23:50


Biology, 30.08.2021 23:50


Physics, 30.08.2021 23:50




