Computers and Technology, 03.06.2021 01:00 mncampbell01
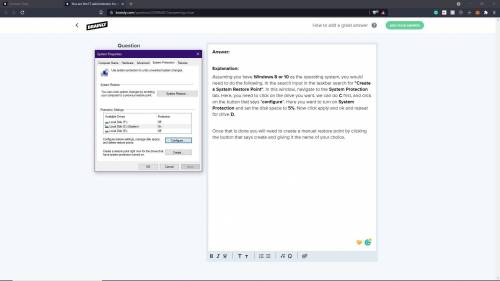
You are the IT administrator for a small corporate network. The employee in Office 1 occasionally needs a previous version of her report files. You need to configure her computer so that you can restore the computer to a point in time if needed. In this lab, your task is to complete the following: Turn on system protection on the C: volume and set a maximum of 5% of disk space for system protection. Turn on system protection on the D: volume and set a maximum of 5% of disk space for system protection. Create a manual restore point. When naming the restore point, choose your own name for the restore point.

Answers: 3


Another question on Computers and Technology

Computers and Technology, 22.06.2019 18:30
Kto rozmawia z clamentain przez krótkofalówke w the walking dead w 4 epizodzie
Answers: 1

Computers and Technology, 24.06.2019 21:50
The use of phrases, fragments, and punctuation can influence the mood of a passage; keeping this in mind, how would you describe the mood of the followingpassage? "fog on the essex marshes, fog on the kentish heights, fog creeping into the cabooses of collier-brigs; fog lying out on the yards, and hovering in the riggingof great ships; fog drooping on the gunwales of barges and small boats. fog in the eyes and throats of ancient greenwich pensioners, wheezing by thefiresides of their wards; fog in the stem and bowl of the afternoon pipe of the wrathful skipper; fog cruelly pinching the toes and fingers of his shivering little'prentice boy on deck." (5 points)
Answers: 2

Computers and Technology, 25.06.2019 14:40
Which of the following is the definition of role-based access control ( rbac)? (a) ensures that data has not been accidentally or intentionally modified without authorization. (b) access control system where rights are assigned based on a user’s role rather than his or her identity. (c) ensures that private or sensitive information is not disclosed to unauthorized individuals. (d)the principle in which a subject—whether a user, an application, or another entity—should be given the minimum level of rights necessary to perform legitimate functions.
Answers: 2

You know the right answer?
You are the IT administrator for a small corporate network. The employee in Office 1 occasionally ne...
Questions

Mathematics, 08.04.2021 15:00

Social Studies, 08.04.2021 15:00


Chemistry, 08.04.2021 15:00



English, 08.04.2021 15:00

Chemistry, 08.04.2021 15:00


Mathematics, 08.04.2021 15:00

Mathematics, 08.04.2021 15:00

History, 08.04.2021 15:00


Mathematics, 08.04.2021 15:00

Mathematics, 08.04.2021 15:00




Mathematics, 08.04.2021 15:00