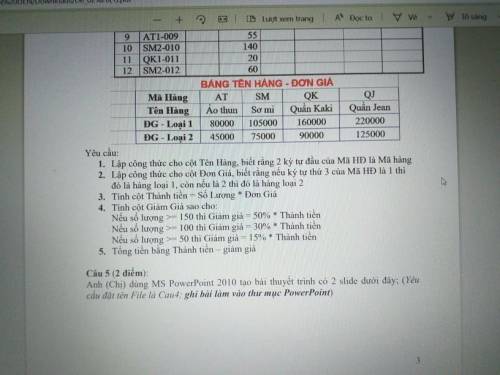
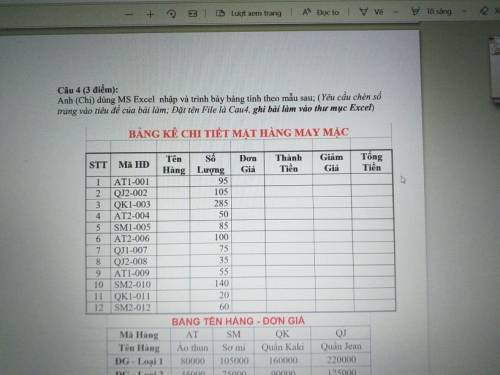
Mọi người giúp em với ạ
...

Answers: 3


Another question on Computers and Technology

Computers and Technology, 21.06.2019 21:30
Asuccessful format string attack attempted to steal user account information by reading from unauthorized memory. answer the followings with proper explanation a)this attack will lead to violation of which security policies?
Answers: 2

Computers and Technology, 22.06.2019 13:50
The instruction ishl (shift left integer) exists in jvm but not in ijvm. it uses the top two values on the stack, replacing the two with a single value, the result. the sec- ond-from-top word of the stack is the operand to be shifted. its content is shifted left by a value between 0 and 31, inclusive, depending on the value of the 5 least signifi- cant bits of the top word on the stack (the other 27 bits of the top word are ignored). zeros are shifted in from the right for as many bits as the shift count. the opcode for ishl is 120 (0x78).a. what is the arithmetic operation equivalent to shifting left with a count of 2? b. extend the microcode to include this instruction as a part of ijv.
Answers: 1

Computers and Technology, 23.06.2019 10:30
How would you categorize the software that runs on mobile devices? break down these apps into at least three basic categories and give an example of each.
Answers: 1

Computers and Technology, 23.06.2019 12:30
What is the difference between the internet and the world wide web?
Answers: 1
You know the right answer?
Questions

History, 27.09.2021 02:00

Social Studies, 27.09.2021 02:00

Social Studies, 27.09.2021 02:00

Mathematics, 27.09.2021 02:00

Physics, 27.09.2021 02:00

Mathematics, 27.09.2021 02:00


Mathematics, 27.09.2021 02:00

Mathematics, 27.09.2021 02:00

Mathematics, 27.09.2021 02:00


Mathematics, 27.09.2021 02:00

Computers and Technology, 27.09.2021 02:00

History, 27.09.2021 02:00

Mathematics, 27.09.2021 02:00

World Languages, 27.09.2021 02:00