Computers and Technology, 17.01.2022 06:40 Annabel9554
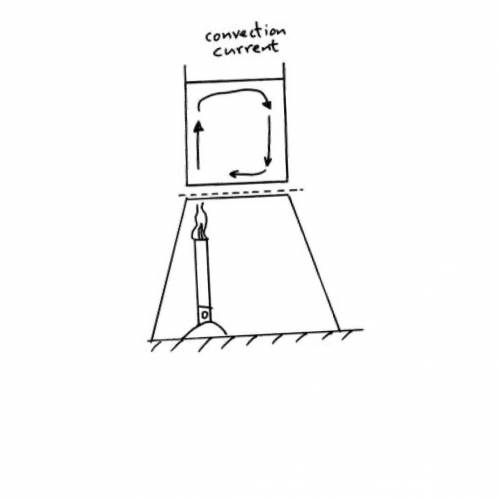
Why do cooler substances have a tendency to sink?

Answers: 1


Another question on Computers and Technology

Computers and Technology, 22.06.2019 14:50
Drag each label to the correct location on the image list the do’s and don’ts of safeguarding your password. a. keep yourself logged in when you leave your computer.b. don’t write your password down and leave it where others can find it.c. share your password with your friends.d.each time you visit a website,retain the cookies on your computer.e. use a long password with mixed characters.1. do's 2. don'ts
Answers: 2

Computers and Technology, 23.06.2019 11:50
While preforming before operation pmcs, you notice the front right tire appears slightly under-inflated. what is the proper action?
Answers: 3

Computers and Technology, 25.06.2019 05:10
Write a program that asks for 'name' from the user and then asks for a number and stores the two in a dictionary (called 'the_dict') as key-value pair. the program then asks if the user wants to enter more data (more data (y/n)? ) and depending on user choice, either asks for another name-number pair or exits and stores the dictionary key, values in a list of tuples and prints the list. note: ignore the case where the name is already in the dictionary. example: name: pranshu number: 517-244-2426 more data (y/n)? y name: rich number: 517-842-5425 more data (y/n)? y name: alireza number: 517-432-5224 more data (y/n)? n [('alireza', '517-432-5224'), ('pranshu', '517-244-2426'), ('rich', '517-842-5425')]
Answers: 3

Computers and Technology, 25.06.2019 10:00
Which of the following methods could be considered a “best practice” in terms of informing respondents how their answers to an on-line survey about personal information will be protected? the investigator uses the informed consent process to explain how respondent data will be transmitted from the website to his encrypted database without ever recording respondents’ ip addresses, but explains that on the internet confidentiality cannot be absolutely guaranteed. respondents are informed that investigators will try to keep their participation confidential; however, confidentiality cannot be assured. the investigator uses the informed consent process to explain her institution’s method for guaranteeing absolute confidentiality of research data. respondents are informed that a research assistant will transfer all the research data to a password-protected computer that is not connected to the internet, via a usb flashdrive. the computer is located in a research team member’s office.
Answers: 2
You know the right answer?
Why do cooler substances have a tendency to sink?...
Questions

Biology, 23.09.2019 05:20

Geography, 23.09.2019 05:20

Mathematics, 23.09.2019 05:20


Business, 23.09.2019 05:20


Mathematics, 23.09.2019 05:20



Mathematics, 23.09.2019 05:20

Mathematics, 23.09.2019 05:20



Mathematics, 23.09.2019 05:20





Computers and Technology, 23.09.2019 05:20

Social Studies, 23.09.2019 05:20