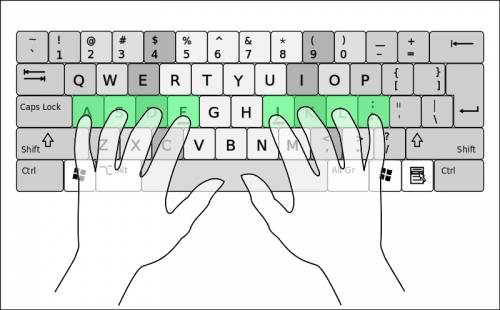
Which letters appear in the home row on a keyboard?
a. q, w, e, r, t, y, u, i
b. p, o,...

Computers and Technology, 26.08.2019 20:30 neariah24
Which letters appear in the home row on a keyboard?
a. q, w, e, r, t, y, u, i
b. p, o, i, u, y, t, r, e
c. a, s, d, f, g, h, j, k, l
d. z, x, c, v, b, n, m

Answers: 2


Another question on Computers and Technology

Computers and Technology, 23.06.2019 08:30
All of these are true about using adhesive except: a. dissimilar materials can be joined. b. mixing tips are product and material specific. c. a specific application gun may be required. d. two-part adhesives are dispensed using two mixing tips
Answers: 3

Computers and Technology, 23.06.2019 09:00
Which best describes the role or restriction enzymes in the analysis of edna a. to break dna into fragments that vary in size so they can be sorted and analyzed b. to amplify small amounts of dna and generate large amounts of dna for analysis c. to purify samples of dna obtained from the environment so they can be analyzed d. to sort different sizes of dna fragments into a banding pattern that can be analyzed
Answers: 1

Computers and Technology, 25.06.2019 08:00
In researching his history report about the civil war, why is ariq most likely to use secondary data than primary data? secondary data provides a starting point to find primary data. secondary data is easier and less time consuming to find. secondary data is always more reliable and credible. secondary data eliminates the need for other research.
Answers: 1

Computers and Technology, 25.06.2019 10:00
Which of the following methods could be considered a “best practice” in terms of informing respondents how their answers to an on-line survey about personal information will be protected? the investigator uses the informed consent process to explain how respondent data will be transmitted from the website to his encrypted database without ever recording respondents’ ip addresses, but explains that on the internet confidentiality cannot be absolutely guaranteed. respondents are informed that investigators will try to keep their participation confidential; however, confidentiality cannot be assured. the investigator uses the informed consent process to explain her institution’s method for guaranteeing absolute confidentiality of research data. respondents are informed that a research assistant will transfer all the research data to a password-protected computer that is not connected to the internet, via a usb flashdrive. the computer is located in a research team member’s office.
Answers: 2
You know the right answer?
Questions




Mathematics, 30.05.2020 10:58





Mathematics, 30.05.2020 11:57





Business, 30.05.2020 11:57



Social Studies, 30.05.2020 11:57