Answers: 1


Another question on English

English, 22.06.2019 00:00
The overwhelming majority of the peoples and nations of the world today want to live in peace
Answers: 1

English, 22.06.2019 10:30
What is the origin of the word renaissance? a. it comes from the word rebirth. b. it comes from the word revival. c. it comes from the word reason. d. it comes from the word redeem.
Answers: 1

English, 22.06.2019 10:50
In act v of a midsummer night's dream, quince presents the prologue for “pyramus and thisbe.” when he finishes, hippolyta comments: indeed he hath played on his prologue like a child on a recorder—a sound, but not in government. which tone does the simile “played on his prologue like a child on a recorder” create? it creates a sad, wistful tone by comparing quince’s performance to a beautiful tune. it creates a surprised tone by comparing quince’s performance to an eloquent speech by a government official. it creates a relaxed tone by comparing quince’s performance to lovely recorder music. it creates a humorous tone by comparing quince’s performance to a child playing an instrument badly.
Answers: 3

English, 22.06.2019 15:50
Read the sample student paragraph that addresses a counterclaim. some claim that the internet both invades and compromises one’s right to privacy. however, this is ridiculous. the internet is only as invasive as one allows it to be, particularly since there are laws to protect people’s privacy. exercising caution when supplying personal information online is the most vital step in protecting one’s privacy. any information you do not feel comfortable sharing online should not be shared, and sensitive information should only be provided to trusted organizations. additionally, some states have already enacted privacy laws that model the federal privacy act of 1974, ensuring that information collected for one purpose may not be used—or sold—for other purposes without first notifying the individual to whom the data belongs. the first and most important protector of an individual’s information is that individual. people whose personal information is not properly protected only have themselves to blame. what evidence weakens the counterclaim in this paragraph? the internet is only as invasive as one allows it to be. exercising caution is the best way to protect one’s privacy online. some states have already enacted online privacy laws. it is the individual’s fault when personal information is unprotected.
Answers: 2
You know the right answer?
Please help me I need to
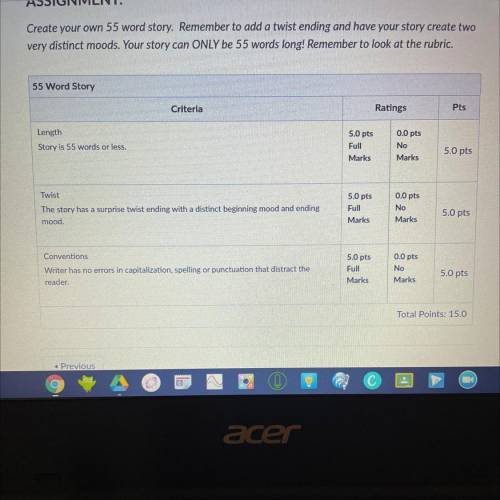
Create my own 55 word story. Remember to add a twist ending and have your...
Questions

History, 17.01.2020 09:31

Mathematics, 17.01.2020 09:31

History, 17.01.2020 09:31

Chemistry, 17.01.2020 09:31

Chemistry, 17.01.2020 09:31


History, 17.01.2020 09:31


English, 17.01.2020 09:31


Biology, 17.01.2020 09:31

History, 17.01.2020 09:31


Health, 17.01.2020 09:31




Mathematics, 17.01.2020 09:31

Health, 17.01.2020 09:31